Cyber security refers to every aspect of protecting an organization and its employees and assets against cyber threats. As cyberattacks become more common and sophisticated and corporate networks grow more complex, a variety of cyber security solutions are required to mitigate corporate cyber risk.
At Remm Technologies, we developed and partnered with industry-leading cybersecurity platform that tailors itself to industry-specific needs.
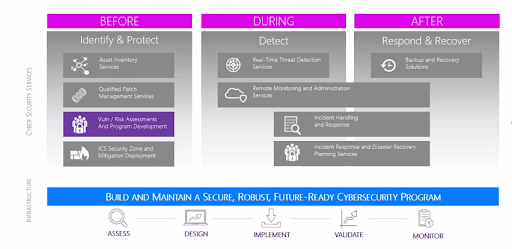
A Holistic Approach to Industrial Cyber Security
Securing Hybrid Cloud with the Vectra platform and services
The adoption of hybrid cloud has led to an increased attack surface, making it easier for attackers to bypass prevention controls, infiltrate, compromise credentials, gain privileged access, move laterally and exfiltrate sensitive corporate data while largely going undetected. In fact, Vectra research found that 72% of security leaders think they may have been breached but don’t know it. Put another way, “we don’t know where we are compromised – right now.”
We call this the unknown.
Why Vectra
Pioneering AI security


Security & Compliance
Identify, remediate and protect against security threats.
Security Not Just for SecOps
IT managers simply can’t afford to ignore security as security and compliance incidents can cause performance problems (Enterprise Management Associates).
A lack of security awareness among network teams can lead to blind spots when investigating the root cause of service issues.
Identify, Remediate and Protect against Security and Compliance Risks

Gartner finds that 88% of respondents view cybersecurity-related risk as a business risk, not just a technology risk. The rise of remote work and increased use of mobile devices and distributed cloud services have expanded the threat landscape for organizations. Costly ransomware attacks, data breaches, and deeply embedded supply chain vulnerabilities have become common occurrences in the corporate sphere. Unpatched network vulnerabilities remain a prominent attack vector exploited by ransomware groups. Shadow IT regularly introduces applications and software that IT is often unaware of and can create unknown security vulnerabilities.
We’d love to schedule a meeting with your team to understand your use case better and showcase our solution to you. Pls suggest a convenient time slot for the same send an email ruth.c@remmtechnologies.com
